Generally, iPhones are considered more secure than Android devices.
Apple’s closed ecosystem and strict App Store policies limit the risk of malware, and its centralized software updates ensure better security. In contrast, Android’s openness allows users to install apps from various sources, and updates are often rolled out at different times, making it more vulnerable to attacks.
However, iPhones aren’t immune to security flaws. Hackers occasionally find ways to exploit them, as seen in Apple’s latest advisory. The company recently discovered that a vulnerability in iOS had been exploited for over a year. While a fix has now been released, reports suggest that hackers may have already targeted high-value individuals.
GET SECURITY ALERTS, EXPERT TIPS — SIGN UP FOR KURT’S NEWSLETTER — THE CYBERGUY REPORT HERE
A woman on her iPhone. (Kurt “CyberGuy” Knutsson)
What you need to know
Apple has uncovered hackers exploiting a vulnerability in iOS that appears to have been lingering for more than a year. The vulnerability is a “zero-day” flaw, meaning criminals may have already exploited it, according to the latest security advisory from the company. Zero-day flaws like this are especially dangerous because they are exploited before developers can issue fixes. Apple confirmed this marks its first zero-day patch of 2025. The vulnerability affects iPhones dating back to 2018’s XS model, as well as newer iPads, Macs, and even the Vision Pro headset.
The vulnerability, tracked as CVE-2025-24085, resides in Apple’s Core Media framework, a software layer responsible for processing multimedia files. A “use after free” memory corruption error enabled hackers to manipulate the system into executing unstable code, granting them elevated privileges to bypass security protocols. Apple’s advisory suggests hackers weaponized the flaw through malicious apps disguised as legitimate media players. These apps likely abused the Core Media framework by triggering corrupted files, enabling attackers to infiltrate devices.
The attacks reportedly targeted iOS versions predating 17.2, released in December 2023, meaning the vulnerability may have been active since late 2022. Security experts speculate that hackers focused on high-value individuals — such as activists, executives or journalists — to avoid detection. The prolonged stealth of the campaign underscores the challenges of identifying sophisticated, narrowly tailored exploits.
This underscores the critical need for you to update your devices to iOS 17.2 or later, as these versions include essential fixes to safeguard against this actively exploited vulnerability.
Apple’s iOS 17.2 update included patches for several vulnerabilities. (Kurt “CyberGuy” Knutsson)
HOW TO PROTECT YOUR IPHONE & IPAD FROM MALWARE
Apple’s response to the vulnerability
In response, Apple has released fixes across its ecosystem, including iOS 18.3, macOS Sequoia, watchOS, tvOS and VisionOS. You should update your devices as soon as possible to stay protected. To install the update on your iPhone or iPad:
- Go to Settings.
- Tap General.
- Click Software Update.
- Click Update Now or Update Tonight.
Pro Tip: I recommend you click Update Now and also turn on Automatic Updates to stay covered in the future.
WHAT IS ARTIFICIAL INTELLIGENCE (AI)?
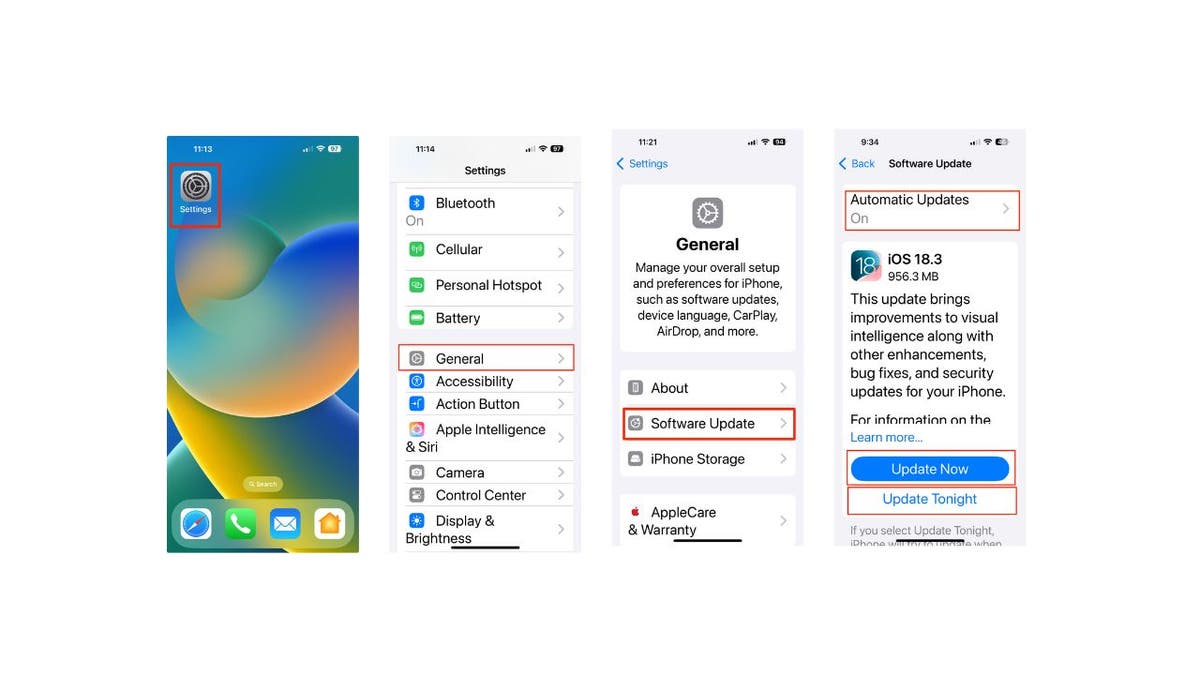
Steps to update software on an iPhone. (Kurt “CyberGuy” Knutsson)
While Apple has patched this issue, it’s a reminder that staying on top of updates is key. Hackers are always looking for security gaps, so keeping your software up to date is one of the best ways to stay safe.
SCAMMERS FOUND A SNEAKY WAY TO BYPASS YOUR IPHONE’S SAFETY FEATURES
7 ways to keep your iPhone safe
Protecting your iPhone requires proactive security measures. By following these seven essential steps, you can significantly reduce the risk of cyber threats and keep your personal information secure.
1. Keep your iPhone updated: I can’t say this enough. Updating your iPhone regularly is one of the most effective ways to protect it from security threats. Apple frequently releases updates that fix vulnerabilities, including critical zero-day flaws.
2. Download apps only from the App Store: To minimize the risk of installing malware, only download apps from the official App Store. Apple’s strict app review process helps prevent malicious apps from being published, but some threats can still slip through. Always verify app details, check reviews and be cautious about app permissions before installation.
3. Enable lockdown mode for extra protection: For those of you who may be at higher risk, such as journalists or executives, Lockdown Mode provides an additional layer of security. This feature limits certain device functionalities to prevent sophisticated cyberattacks. It can be turned on via Settings > Privacy & Security > Lockdown Mode and is especially useful for those concerned about targeted threats.
4. Enable message filtering: Use your device’s built-in filtering options to sort messages from unknown senders. This feature allows you to automatically sort messages from unknown senders, easily filter unread messages and manage your message inbox more efficiently. Here are steps:
- Open Settings.
- Scroll down and click Apps.
- Tap Messages.
- Turn on Filter Unknown Senders
GET FOX BUSINESS ON THE GO BY CLICKING HERE
5. Stay cautious of phishing attacks and install strong antivirus software: Phishing remains one of the most common tactics used by hackers. Be cautious when receiving unsolicited messages or emails on your iPhone, especially those with suspicious links or attachments. Always verify the sender before opening anything. The best way to safeguard yourself from malicious links that install malware, potentially accessing your private information, is to have antivirus software installed on all your devices. This protection can also alert you to phishing emails and ransomware scams, keeping your personal information and digital assets safe. Get my picks for the best 2025 antivirus protection winners for your Windows, Mac, Android and iOS devices.
6. Review your security and privacy settings: Regularly reviewing your iPhone’s security settings can help you maintain strong protection. You should also review app permissions in Settings > Privacy & Security to restrict access to sensitive data, such as location or contacts. Enable Face ID or Touch ID for secure access and turn on two-factor authentication (2FA) for Apple ID and other accounts. 2FA adds an extra layer of security to your accounts by requiring a second form of verification, such as a text message or authentication app, in addition to your password. This significantly reduces the risk of unauthorized access, even if your password is compromised.
7. Invest in personal data removal services: By reducing your online footprint, you make it harder for cybercriminals to obtain your contact information, potentially preventing them from sending you deceptive phishing texts and emails in the first place. While no service promises to remove all your data from the internet, having a removal service is great if you want to constantly monitor and automate the process of removing your information from hundreds of sites continuously over a longer period of time. Check out my top picks for data removal services here.
Kurt’s key takeaway
This iOS vulnerability is a serious reminder of the importance of staying up to date with software updates. If you’re using an iPhone from 2018 or later, make sure you’ve updated to iOS 17.2 or later as soon as possible. Hackers exploited a hidden flaw for over a year, using fake media apps to gain access to devices. While Apple has now patched the issue, the fact that it remained undetected for so long is concerning.
CLICK HERE TO GET THE FOX NEWS APP
Do you think companies like Apple are doing enough to protect you from cyber threats? Let us know by writing us at Cyberguy.com/Contact
For more of my tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter
Ask Kurt a question or let us know what stories you’d like us to cover.
Follow Kurt on his social channels:
Answers to the most asked CyberGuy questions:
New from Kurt:
Copyright 2025 CyberGuy.com. All rights reserved.